Introduction
I'm a Sr. software developer. Few years ago I watched a PBS TV show called "Rise of the Hackers", in which it talked about the vulnerability of the Internet and said traditional password is a weak link in cyber security. That inspired me to do something about it and fix this problem, so I came up with a solution called GATE : Graphic Access Tabular Entry.
GATE is an interception-resistant user authentication system, which means even if someone intercepts/sees you when you log in [ assume he sees/records every detail of your authentication ], he still won't know what your password is.
| Current Password System Problems : [ See details in Password Problem Wake Up Call ⚠️ ] |
| A desktop app to protect passwords from exposure, especially the master passwords of password managers. GATE_For_PM can be used as a password manager too. Free Download & Use. |
| A demo app to compare the weaknesses of traditional password systems to the strengths of the innovative GATE authentication system. Free Download & Use. |
There is a hacker attack every 11 seconds.
Hacked passwords cause 81% of data breaches.
Average total cost of a data breach is now $ 5 million.
Here are the 15 biggest data breaches of the 21st century. A reader saw this site and suggested I include this article about a breach affecting a hotel reservation platform which might harm all of us.
As of July 2020, there are 15 Billion Credentials Currently Up for Grabs on Hacker Forums. World population is now 7.8 Billion, if you take out half of it from poor countries that don't have a lot of computers, there will be around 4 Billion left in developed countries with computers and online accounts, so that means averagely speaking, we all have 3 or 4 accounts breached !
In this video you can see how hackers intercepted user passwords from far away, which seems like a safe distance from the user, yet the hackers were able to figure out user passwords by looking at their finger movements and analyze the data to steal the passwords.
| Have you been told that your passwords are too weak ? Were you asked to lengthen your passwords and use special characters to the point that you can't even remember them with so many accounts ? Weak passwords make systems vulnerable, yet strong passwords make you forget. Is there a way to keep the passwords simple and yet still make the system secure ?! |
| Requirements for passwords that make them hard to remember : lowercase, uppercase, numbers and special characters, at least 8 digits long, change every 2,3 months. |
| No matter how strong a password is, it is still prone to peeking, keylogging, phishing and dictionary attack. |
| Traditional password is getting easier and easier to hack, with the advance of modern technology, hackers could easily get hold of high resolution hidden video cameras, or trick users into downloading key loggers. |
Reset Password
Password Rant
How Keylogger Works
Hacker Talking About Stealing Passwords
You might ask, how about password managers ? Read on ...
Before You Use a Password Manager
Password managers aren't all they're cracked up to be. Here's why
Passwords have been used for thousands of years. Since the days of the Arabian Nights fables when Ali Baba overheard the Forty Thieves commanding 'Open Sesame' to access their riches, through PIN privacy at ATM machines, to server to server cyber capture of personal and financial information in our high-tech world, password interception has been recognized as a fundamental threat to account security. A single capture, whether decrypted or not, can lead to complete account infiltration.
How Password Is Leaked
Snowden on Passwords
Because of the password problems, there is a trend to use bio-metrics to replace passwords, yet a lot of places are starting to ban bio-metrics. Bio-metrics also compromises your privacy.
San Francisco Bans Facial Recognition Technology
'This Is a Bombshell': Facial Recognition Data Collected by US Customs Agency Hacked
Breach of Biometrics Database Exposes 28 Million Records Containing Fingerprint and Facial Recognition Data
3-D printers help override biometric security measures
007 Fakes Fingerprint
Deal With Iris Scanning
| Therefore password is still a better option IF WE CAN OVERCOME ITS WEAKNESS. The problem with traditional passwords is their obviousness, and this obviousness can easily lead to interception during the login process [ peek over the shoulder, key logging, video recording ... ]. |
Keypad Password Obviousness
Cellphone Password Obviousness
To overcome this shortcoming, there is a new category of user authentication systems that hides user pins during the authentication process therefore protecting user pins from exposure. Among them is a system called GATE [ Graphic Access Tabular Entry ], it not only hides user pins among other symbols, but it took one step further to protect user pins by introducing the concept of missing pins : Here is how GATE works
Demonstration
As a proof-of-concept I implemented GATE into an application :
There are free GATE demo apps, I encourage you to play with them to find out for yourself about the details you are looking for, I don't want you to take my word for it, get a hands on experience with the GATE system and you can explain it better to others after you have the experience. Think of it as a word puzzle game, it's fun to play with.
Here are where to find the 3 demo versions :
[a] Online web version : User data is erased over night, so if a user created an account today, and played with it, the account won't exist tomorrow. He will have to re-create it.
[b] Android version : This is the latest version, with colors, I've tested it on my Samsung Galaxy phone, it looks good, it should also run on other Android devices.
[c] Java Swing desktop version : This is the ORIGINAL implementation, done few years ago, it may not look as fancy as the other 2 versions, but it has something the other 2 versions don't have : Auto demo with highlighted user pins on screen and "Text Login" tab which shows the internal data flow of the GATE system, how the symbols are passed around, and if the communication is intercepted, what the hackers will see, from there you can play the hacker's role and try to guess the GATE passcode [ assume your friend created the passcode, you didn't know but you intercepted the transmission ].
Details
Purpose Of The Invention
The intention of this invention is to prevent passcode [ similar to traditional password, but can include symbols ] from being intercepted during the process of entering and transmitting. With the protection of the invention, user will not be afraid of being watched by a hacker while entering the information, because the hacker will not know the passcode. Even after many times of observing/intercepting the user entering the login info, the hacker will still remain unable to figure out the passcode.
Rules Of The GATE [ Graphic Access Tabular Entry ] System
The newly patented GATE system overcomes the weaknesses of traditional passwords. Special characters are part of the GATE design. It uses tokens [ groups of symbols, displayed on buttons ] to let user enter user pins from passcode, each token has several symbols, some randomly selected user pins are included in these tokens. It is impossible to tell which symbols in the tokens are valid user pins, which are non-user pins, thereby increasing password strength exponentially. Some user pins might not even appear in the tokens, in that case user can and must enter random tokens in place of those pins, and this uncertainty makes guessing your passcode much harder.
This approach is like hiding a needle in a haystack. Instead of entering one digit at a time like the traditional approach, the GATE system enters multiple symbols at a time as a token. Only someone with knowledge of the passcode will be able to tell if the token entered is valid or not.
The symbols used to create the passcodes are of different types that are preferably grouped into 4 groups that will be referred to herein as "dimensions". Each dimension containing 36, 50 or 100 symbols [customizable]. During a login process, 9, 10, 16 [customizable] tokens are displayed for the user in a tabular format, with each token containing a symbol from each of the four dimensions of symbols. A given symbol is preferably displayed in only one token (i.e., if the symbol appears in one token it does not appear again in another token).
In order to prevent a hacker from finding out the pins in the passcode over time, the number of randomly generated tokens presented to the user is preferably less than the number of symbols in each dimension. For example, if each of the 4 dimensions contain 36 symbols, one could choose to only present 9 tokens to the user in a 3 x 3 table, or in a 2 x 5 table [ more suitable for mobile display ] with 10 tokens. The result of this is that there is no guarantee that a user pin will even appear in a token. In this embodiment, if the user is attempting to login and one or more pins in the user’s passcode is not present in any of the tokens, then the user selects any token as a "wildcard" token for the pins that are not present in any of the tokens (such that the pin position of the selected wildcard token corresponds to the pin position of the missing passcode pin). This makes a hacker's guess work much more difficult, because there may be a randomly chosen token in place of one of the user’s pins that does not actually contain the pin.
Another benefit of using less tokens than the number of symbols in the 4 dimensions (e.g., using 16 tokens when the number of symbols in the 4 dimensions is 36) is that it makes it easier for users to quickly find out whether the pre-selected pins are in the tokens or not, and the screen looks simpler to the user.
Each dimension of symbols will have a fixed location on the token/button, 1st dimension has all the numbers, they will only appear on the upper left corner of each token/button, 2nd dimension has all the alphabets, they will only appear on the upper right corner of the tokens/buttons ... so on. Therefore if a user passcode is all numbers, the user only needs to concentrate on the upper left of each token to see if his pins are on the screen, and if his passcode are all characters like "pdacf", he needs to only look at the upper right corner of each token to locate his pins, they won't appear in other 3 corners. This will help the user to quickly enter his passcode.
In GATE_4 there are 4 symbols on each token/button, in GATE_5 there are 5 symbols on each token/button.
The GATE algorithm randomly picks some pins from user passcode according to the user Id saved on the server, at least one user pin will definitely show up in the tokens table, but this can be customized to at least 2 or 3 pins must show up. There is a tendency to think more pins show up will make it more secure to defeat random pin attack, but you also need to keep in mind, if the login sessions are intercepted [ basic assumption of the GATE system ], the more pins show up each time, the more likely a hacker can do a comparison of the intercepted sessions and quickly find out which are the user pins, so there is a trade off, need to find the balance point.
For example, if my passcode is : Ⓘ ♥ 2 ✉
The traditional approach is to enter the following symbols one at a time : Ⓘ , ♥ , 2 , ✉
If a hacker stands next to me and watches me enter these symbols from the screen, he can easily remember the sequence and therefore steal my passcode.
But if I enter the following tokens [ each has 4 symbols ] one at a time :
| Token 1 | Token 2 | Token 3 | Token 4 | |
| Key Tokens : | ||||
Then the passcode is hidden in the symbols in each token, and the hacker won't be able to tell which ones of the symbols in the tokens represent the correct passcode.
You might think, well, the passcode is still among the symbols in the tokens, and if a hacker observes enough times, he can guess which symbols in the tokens are part of the passcode. OK, that's a great observation, but see if you can figure out the passcode from the following subsequent successful login sessions :
| Token 1 | Token 2 | Token 3 | Token 4 | |
| 1st time login tokens : | ||||
| 2nd time login tokens : | ||||
| 3rd time login tokens : | ||||
The passcode remains the same, and the above sessions are all successful login attempts with valid tokens, but the hacker may have a hard time guessing the correct passcode due to the rules of this innovative new method to authenticate users. The token are automatically generated by the new method's algorithm, and because the user and the system know the passcode, they know which tokens are valid. Since the hacker is unaware of the passcode, he will not know which ones among them are valid tokens to select. And the next time when a user logs in, the system will present a different set of tokens with randomly generated symbols in them.
In the tokens table, some user pins might not even appear, but at least one user pin will definitely be in the tokens table. When a user pin is missing in the table, user can and must enter a random token in place of that pin, and this uncertainty makes guessing your passcode much harder and therefore greatly increases passcode safety.
To simplify the explanation, here is an easy example; let's say Alice wants to authenticate Bob over a network, while Eve is eavesdropping on their communication. Anything sent from Alice to Bob, or from Bob to Alice, Eve will know.
Both Bob and Alice know that Bob's passcode is "I ♥ U". Let's call each symbol a pin. So in order to authenticate Bob, he needs to transfer these 3 pins to Alice over the network.
The traditional way is for Bob to pass the 3 pins "I" , "♥" , "U" to Alice over the network, and Eve can easily and obviously see the 3 pins in the passcode.
But Alice is clever enough not to show her communication with Bob in plain sight. Because both Alice and Bob know what Bob's pins are, Alice would present Bob with a group of tokens, generated by token generation rules, with at least one of Bob's pins in the tokens, and ask Bob to pick the correct ones to enter his pins (each token has several symbols in it).
For example, Alice can send Bob the following tokens for Bob to pick and enter his pins :
Token 1 : 3 I #
Token 2 : 5 P &
Token 3 : 9 U @
Token 4 : 6 W +
Now looking at the above 4 tokens, Bob selects the appropriate tokens to enter his pins according to token selection rules : if a pin appears in a token, he must select that token to enter the pin, but if a pin is not in any of the tokens, he can and must select a wildcard [ any ] token to enter that pin.
So Bob goes through his passcode and enters his 3 pins one by one. His first pin is "I", so he scans the above 4 tokens and tries to find a token that contains this pin, the first token [ 3 I # ] contains this pin, so he selects this token to enter his first pin.
Now Bob needs to enter his second pin "♥", but it is not in any of the tokens, so according to the token selection rules, he can and must pick a wildcard [ any ] token to enter this pin, so he selects the 4th token [ 6 W + ].
For the 3rd and last pin "U", Bob goes through the 4 tokens and finds it in the 3rd token, so he selects it [ 9 U @ ] to enter his 3rd pin.
As a result of the above selection process, Bob entered 3 tokens :
Token 1 : 3 I #
Token 4 : 6 W +
Token 3 : 9 U @
These 3 tokens will be sent over the network to Alice for validation, once Alice gets the 3 tokens entered by Bob, she will go through each one of them and see if they are valid according to the token selection/validation rules.
Alice knows that Bob's first pin is "I", so she checks all the 4 tokens she sent to Bob to see if the symbol "I" is in any of them. Since it's in the 1st token, and Bob did enter that token as the first pin, it's valid.
Then Alice looks at Bob's 2nd pin "♥". Since it's not in any of the 4 tokens that she sent to Bob, it must be entered by selecting a wildcard random token, and Bob did enter a wildcard token, so it's valid too.
For the 3rd and last pin in Bob's passcode : "U", Alice goes through all the tokens she sent to Bob and finds it in the 3rd token, and she sees that Bob did enter the 3rd token [ 9 U @ ] for that pin, therefore the 3rd pin Bob entered is also valid.
Since the tokens Bob entered are all valid, his authentication is validated. Otherwise, if any token Bob entered is invalid, or if Bob entered more or less tokens than the pin count [3] in his passcode, then he will be denied access.
But because Eve is eavesdropping on their communication, she can see the tokens entered by Bob : [ 3 I # ] , [ 6 W + ] and [ 9 U @ ], but she can not tell which symbols among them are Bob's true passcode. And if she intercepts again next time when Bob tries to login, she will get another set of random symbols, and she will still be unable to figure out Bob's real passcode.
If you are looking for more details, you can find it here.
In the GATE system, available symbols for users to select to create their password is beyond the symbols on the regular keyboard, therefore in the GATE system the word "passcode" is used in place of password. The symbols used in a GATE system are customizable according to the requirements of the organization that uses GATE, this abundance of symbols will give users of the GATE system more flexible choice to use their imagination for creating easy to remember passcodes. Since the symbols are beyond dictionary, GATE can not be dictionary attacked.
Based on user passcode choice, GATE server renders passcode entry buttons/tokens on a screen, rendering multiple characters per button/token. User pins are mixed in among the symbols displayed in the buttons/tokens. Some user pins might be intentionally missing on the screen, when a pin is missing, user can and must select a wildcard button/token for that missing pin, this security feature makes hacker's guess work much harder. When button/token selection is made by a user there is no way for an observer to know the actual passcode due to the multiple characters per button/token.
Each subsequent rendering of buttons/tokens by the server will be unique, based on the GATE algorithm, ensuring button/token selection cannot simply be repeated based on button/token location in order to infiltrate an account.
Due to the rendering process required in order to present passcode buttons/tokens to a user, a server has to already know the passcode of the user in order to render an appropriate array of buttons/tokens.
Therefore bogus or malicious servers will not be able to render an appropriate array of buttons/tokens to a user, which allows the user to recognize whether or not the screen he is looking at is being controlled by the appropriate body.
| GATE can use short and easy to remember passcodes to defeat peeking, keylogging, phishing and dictionary attack. Anywhere there is a need for access control, there is a need for the GATE system, including but not limited to : door access, safe box, PC, mobile phone, web login, ATM, weapons system, facilities [ infrastructure ] ... |
Basically what GATE is trying to achieve is the following :
[a] Solve the main problem current password system has : user pin exposure during the authentication process, by peeking over the shoulder, phishing, keylogger or video camera.
[b] Ease requirements for passwords that make them hard to remember : lowercase, uppercase, numbers and special characters, at least 8 digits long, change every 2 ,3 months ...
[c] Avoid dictionary attack.
[d] Avoid higher costs of bio-metrics, compromising of privacy and yet still not safe for security.
I welcome you to do a deep SIDE-BY-SIDE COMPARISON of the current password systems and the GATE system in the following areas :
[a] Peek-over-the-shoulder
[b] Keylogger
[c] Hidden camera
[d] Wire tapping
[e] Password/passcode requirements
[f] Phishing
[g] Dictionary attack
And see which one is better in each area. You can pretend to be [ or maybe you already are ?! ] a hacker, setup a few hidden cameras, pointing them at a test user's keyboard and screen, ask him to login to a regular account and then login to a GATE account, try 3 times for each case, then play back the videos, see if you can guess his password in either account. A hacker test like this.
There are 3 elements in the user authentication field :
[a] Who you are : Fingerprint, facial scan, iris scan ...
[b] What you have : PC, cellphone, key fob ...
[c] What you know : Password, pin ...
Since there is a weakness in the current password system, there is a trend to replace password with the other 2, i.e. use bio-metrics + a device to authenticate user.
THIS IS VERY DANGEROUS ! Because a hacker can get hold of your bio-metrics data and your device, then login WITHOUT your consent. Imagine in a 007 / "Mission: Impossible" scenario, the hacker can get close to the user as a boy/girl friend, setting up some hidden cameras, record all his communications, especially his master password in his password manager, copy the fingerprint, and have access to his device while his is in the shower, drunk or asleep, then use the stolen bio-metrics data and login to his device while he is unconscious. I would imagine it's possible to use a hidden camera and point at the user while he is conscious [ but not knowing that a hidden camera is using his face ] to login.
Therefore the 3rd element [ password ] is still important, it's the knowledge the user has, and it shows his intention when he logs in with this knowledge. The problem we are facing is how to authenticate the user WITHOUT EXPOSNIG THIS KNOWLEDGE.
And because of this weakness, all the other problems follow : requirements of uppercase, lowercase, numbers, special characters, has to be at least 8 digits long, has to change password every 2,3 months ... Which makes it hard for the user to remember, so instead of solving the problem, the requirements made the situation worse. Then comes password manager, and the user would put all his eggs in one basket ... and when the master password gets breached, all passwords are stolen.
Some might ask : "How about a multifactor authentication like this ?" Well, as you can see in the video, if a hacker can steal the 1st answer, then he can also steal the 2nd answer, so the more facts you expose, the more secrets he will steal from you. The point is not how many secrets are there that you know, but how not to expose them during authentication.
So to solve the above problems of current password systems, GATE targets the root cause of the problem : password exposure during the authentication process. Once this main problem is solved, all the other problems are also solved.
Some also asked : "How is GATE more secure than the current system ?" The answer is : current system got intercepted all the time, one interception [ keylogger / video recording ], and the password is gone. Current password system CAN NOT WITHSTAND one shot [ like a regular glass ], while GATE can withstand multiple [ N ] interceptions [ like a bulletproof glass ], so mathematically speaking N / 0 = ∞.
GATE is MUCH MORE SECURE than the current system. In a [ cyber ] battlefield, would you like to ride in a car with regular glass, or would you rather ride in a car with bulletproof glass ?!
Since I'm a Sr. Java developer, the sample apps are implemented in Java, but the concept of GATE can be implemented in any language, and run on any OS, there is no image to upload or maintain, all the symbols are part of standard Unicode.
Paper
A paper titled Cyber Security Innovation : Bye Bye "Open Sesame". Hello "GATE" ^_^ ! was presented at the PenTest Magazine online on page 72 in July 2017.
A more recent paper titled Graphic Access Tabular Entry [ GATE ] : An Interception-resistant Authentication System And Method is also available.
Awards
In the last few years GATE has won 7 international cybersecurity innovation awards. Among them is the "Cybersecurity Innovation Award" at 2017 International Cyber Security and Intelligence Conference [ ICSIC ] on November 7th - 8th, 2017 in Toronto, Canada. Also the "Innovation Award In Cyber Security" from IET [ Institution of Engineering and Technology ] on 14 November 2018, in London.
The Institution of Engineering and Technology (IET) is a multidisciplinary professional engineering institution. The IET membership is currently in excess of 168,000. It represents the engineering profession in matters of public concern and assists governments to make the public aware of engineering and technological issues. It provides advice on all areas of engineering, regularly advising Parliament and other agencies in UK.
|
|
|
|
|||||
|
GATE won "Innovation Award In Cyber Security" at IET on 14 November 2018, in Brewery, London |
GATE won "Global Excellence Awards" at 2020 Info Security Products Guide |
GATE has been selected to the top 100, among more than 2800 technologies collected from all over the world at 2021 ZGC International Technology Trade Conference. |
Q&A
- Q 1. Is GATE something that is in the market right now or just being realized ?
- Q 2. Does the destination computer have knowledge or know how to interpret these symbols ?
- Q 3. About the token, is it a physical token that you have to carry around ?
- Q 4. When using GATE, do you remember letters or symbols ?
- Q 5. What would it take to implement this technology, both in terms of equipment and money ?
- Q 6. How can you use GATE to program machines to authenticate each other ?
- Q 7. How can GATE be used for information encryption and decryption, what encryption algorithm is used ?
- Q 8. Any hashing for the passcode file ?
- Q 9. What about entering a password into a command prompt when trying to connect through ssh remotely ?
Q 1. Is GATE something that is in the market right now or just being realized ?
A : GATE is coming to the market, and available now if you are interested. You can get it in the following formats :
[1] Sample software -- different versions with different levels of functionality and pricing : https://nmjava.com/gate/Software_And_Training.html
[2] Licensing -- contact for details
Q 2. Does the destination computer have knowledge or know how to interpret these symbols ?
A : Only the server that runs GATE has knowledge of the symbols and knows how to interpret them, the client that user logs in is only functioning as input/output device, it knows nothing about how to interpret these symbols, it just passes the info between the server and the user.
Q 3. About the token, is it a physical token that you have to carry around ?
A : No, it's not a physical entity you carry around. I'm just borrowing the word "token" to refer to a group of symbols that are presented to the user, you can easily use other words to mean the same concept : symbols group, or symbol set. The purpose of using a group of symbols is to hide each user pin among other symbols, so the user pin is not obvious to a hacker / observer. When the token [ group of symbols ] is displayed on the screen, they are on a button [ each with 4 symbols ], so in GATE the word token and button are interchangeable. But keep in mind GATE can also do machine to machine authentication, what's passed between the machines are a group of symbols [ token ], in that case nothing needs to be displayed on any screen, and therefore there is no button to be seen, just some tokens being exchanged between the machines.
Q 4. When using GATE, do you remember letters or symbols ?
A : Yes, of course, user has to remember the user Id and pins in the passcode. This is the same as traditional password, you need to know what your user Id is and what the pins are in your passcode. What's different between GATE and traditional password is : instead of entering one pin at a time [ which is easily stolen by a hacker/observer ], GATE enters a group of symbols at a time for each user pin, the user pin is mixed in with other symbols, so it becomes obscure. And only the user and the server know whether the tokens entered are valid or not.
Q 5. What would it take to implement this technology, both in terms of equipment and money ?
| A : | [1] Equipment : no special requirement. Any modern device will be able to run GATE, assuming the following : |
| [A] A graphic display that can show images [ touch screen will be better, but not necessary ] | |
| [B] A mouse [ can be skipped if the display is touch screen ] to point on the display and click to enter info | |
| [2] Money : can get you some or all of the following if you desire : | |
| [A] Training for the GATE system | |
| [B] Sample GATE software to show you how to implement the concept, it's written in Java, different versions/complexity of the software are available with or without [ if you only want to see how it works ] source code at different prices. See web page for details. | |
| [C] Licensing for the patented GATE system |
Contact for details.
Q 6. How can you use GATE to program machines to authenticate each other ?
A : With traditional password, you can use machine A to log into machine B, as long as machine A knows the password, this is the same with GATE, machine A can log into machine B, as long as machine A knows the GATE passcode on machine B. The reason I'm saying this is because some authentication methods only work between human and machine : e.g. finger printing & iris scanning, they can only authenticate human, they can't be used to authenticate a machine. But GATE, like traditional passwords, can be used to authenticate both human and machine.
Q 7. How can GATE be used for information encryption and decryption, what encryption algorithm is used ?
A : It uses the GATE encryption algorithm, it mixes information elements with misinformation elements, then attach valid tokens table and key tokens to the information elements and invalid tokens table and key tokens to the misinformation elements, and sent them out, on the receiver side, authenticate each set of information by checking the attached tokens table and key tokens, then get rid of the misinformation and get the original information. This method is explained in the GATE video : https://www.youtube.com/watch?v=518p2cIbynY
Q 8. Any hashing for the passcode file ?
A : The GATE passcode file is encrypted, not hashed, so the GATE app running on the server can decrypt and read it back to get the user pins, then mix them with other symbols to present them to the user as tokens table. Programmers can select any reliable encryption method they choose, the encryption key can be dynamically generated and it is not saved anywhere so no one can steal it. The encryption key can be generated by mixing some of the following unique and yet stable info : server Id, CPU property, motherboard property, the GATE app Id on the server, hard drive serial number or some other property that is not saved in a file or DB, but the GATE app can get by making a call to the system. That way a hacker won't be able to get the key from a file or DB, and this will make the encryption key safe from being stolen. In case the info gets changed because of a system change [ CPU, motherboard, hard drive failure and need to replace them with a new one and therefore the info used to generate the encryption key needs to change ], then users need to reset their passcodes.
We are forced to update our passwords every 3,4 months with the current password system, with the GATE system, if such changes do happen, just treat it as a forced password update for the sake of safety, shouldn't be too much of an issue, because people are already doing it now with the traditional password system anyway. So the main point is to select some unique [ different from machine to machine, and different from one GATE app to another ] and stable [ so it keeps the same for a long time, therefore users don't have to reset their passcodes too often, assuming you don't change your CPU / motherboard every month ]. The programmer can combine some of the selected properties and get a hashed string, then use that as the encryption key. Therefore this key will be unique when it's running on each machine, even the programmer will not know what the key will be when the GATE runs on a production machine, because when the app runs on development machine, it uses the info from the development environment, but when it's running on a production machine, the info from that environment will be different. Dynamic, unique and stable are the 3 key words here. Sample implementation is in my demo code.
But, if you don't like this approach, you can use a fix string as a key for encryption/decryption, with GATE you have the option to choose either method.
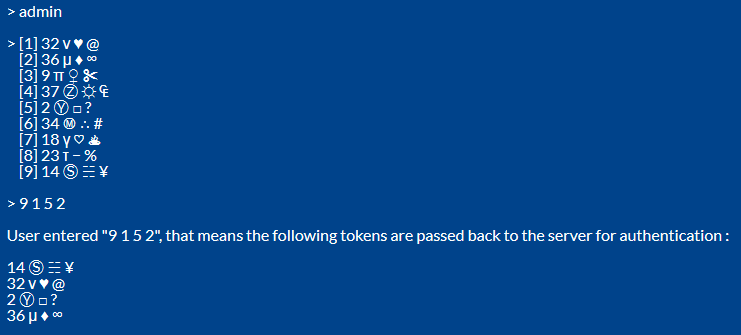
Q 9. What about entering a password into a command prompt when trying to connect through ssh remotely ?
A : It can be done like this : the user first enters Id, the server generates 9 tokens [ like 9 buttons in a UI ], show them to the user on command line, then user enters a number which stands for the index of the token [ each of which may have 4 symbols in that token ], so it looks like this :
Summary
Cybersecurity affects us all, let's make it stronger, and you can help by sharing this site. More and more frequently we read about data breach, how many millions of records got compromised, I used to think that's someone else's problem, has nothing to do with me, but that all changed when Equifax got hacked, I got an email saying my info might be stolen and also read online that we can now apply for compensation. That made me thinking, how many other data breaches would affect all of us, and usually what is disclosed is only the tip of an iceberg, most of them you may never know because the organizations don't want to lose their reputation, and further more, they themselves may not even realize the data breach until 6, 12 months down the road, or maybe never. So where does that leave you ? "In the dark, of course !"
Also, what bothers me more on a daily basis is the password requirements, nowadays an average person all have dozens of accounts, each account has different requirements, I want to come up with a unique password that can log into all accounts, so I don't have too many of them to remember, therefore I tried to combine uppercase, lowercase, numbers and special characters all together into a "golden password", but that didn't work, because some places don't allow special characters, and others must have special characters. And what's more, even after I've come up with a memorable password, it has to be changed every 2 months, THAT DRIVES ME CRAZY ! I wanted to shout : "Who made up these rules, are you nuts, whose side are you on, are you trying to make it so hard for me to remember my passwords that I have to write them down, and easily stolen by the hackers ?!" So I was determined to come up with a way that makes users lives easier, sys admin's environment more secure and hackers' work much harder, and I found it in GATE. Let's get back to the good-old-days, when we can use a 4 to 6 digit passcode and still be SAFE ! It's NOT a dream, definitely doable with the GATE system. Hope others can also see the light at the end of this dark tunnel, and make the digital world a safer place. You can contribute your efforts by sharing this innovative idea, the more people know about it, the more minds are put together to make this "easier, safer digital life" a reality. I've done my part and submitted GATE to multiple places including the NIST, Google and Microsoft, but no response after 2 years, and passwords kept getting stolen ... So if you think this is a viable solution, get your voice heard, or even if you are not sure, then pass this info around and someday, somehow it will reach an expert, a decision maker WHO CAN GIVE GATE A SERIOUS LOOK, do a usability study and see the value in it. Put in your straw to break this [ old password system ] camel's back. WE ALL DESERVE A SAFER AND EASIER LIFE !
Some might ask : "What's in it for me ?"
Great question, here are the ways GATE might benefit you :
[1] As an individual : No more stringent password requirements, a 4 to 6 digit passcode will make your account safe, it's easy to remember and use. You won't fall for the phishing scam, because a GATE server has to know your pins to display proper buttons on the login screen, phishing sites don't know your passcode, and therefore can't generate the buttons for you to login.
[2] As an organization : Sys. admins will have a more secure environment, your organization's data security will be stronger than the ones with traditional password system, hackers will shy away from you and find other easier targets.
[3] As a software developer : With GATE implemented in your software to authenticate user, it will be interception-resistant, be more tolerant to password attacks, make your application more innovative and standout from the crowd, and will be more attractive to security conscious users.
[4] As general public : Enjoy a more secure digital world, live in a safer society.
[5] As a hacker [ let's not forget about him *_^ ! ] : Yes, there is something for him too, no more easy targets, He will have to work MUCH HARDER to steal information ! "Go elsewhere, no easy meal with GATE".
Times have changed, we are now in the 21-century, yet we're still using the age old password system, hackers now have state-of-the-art tools to steal our passwords, we also need better ways to protect ourselves, we need to be a few steps ahead of the hackers, the 3rd element in the authentication area of "what you know" is not only an indispensable part, but it is the most important part of the process, we can not and should not skip it, instead, we need to make it more secure. What we need is rejuvenation, not elimination of the process ! Fixed passwords have the advantage of easy to remember, one-time passwords have the advantage of hard to hack, GATE passcode is a fixed passcode to the user, but from the hackers' perspective, it changes every time, GATE passcodes have the best of both worlds, short and easy to remember, yet secure and hard to hack.
The fact that accounts with traditional passwords will be hacked is a matter of "when" not "if", they are just one hidden camera/keylogger/phishing attempt away from being compromised. Let's wake up to the cruel reality, rather than pretending not to see it by playing ostrich, hackers will see what you don't want to see [ weakness in traditional passwords ] and take advantage of it, a chain is only as strong as its weakest link ! Let's face it and fix this weak link !
I would envision old and new system exist side by side, let users have a choice, if they like the old system's simplicity, use the old login format, but if they value the security of the GATE system, use the GATE login format. Users of the old system will gradually won over by the new system, as traditional password systems are easy targets for the hackers.
