GATE [ Graphic Access Tabular Entry ]
An Interception-resistant Authentication System
Frequently Asked Questions
Q 1. Is GATE something that is in the market right now or just being realized ?
A : GATE is coming to the market, and available now if you are interested. You can get it in the following formats :
[1] GATE IP License
[2] Software And Training - Sample software : different versions with different levels of functionality and pricing
Q 2. Does the destination computer have knowledge or know how to interpret these symbols ?
A : Only the server that runs GATE has knowledge of the symbols and knows how to interpret them, the client that user logs in is only functioning as input/output device, it knows nothing about how to interpret these symbols, it just passes the info between the server and the user.
Q 3. About the token, is it a physical token that you have to carry around ?
A : No, it's not a physical entity you carry around. I'm just borrowing the word "token" to refer to a group of symbols that are presented to the user, you can easily use other words to mean the same concept : symbols group, or symbol set. The purpose of using a group of symbols is to hide each user pin among other symbols, so the user pin is not obvious to a hacker / observer. When the token [ group of symbols ] is displayed on the screen, they are on a button [ each with 4 symbols ], so in GATE the word token and button are interchangeable. But keep in mind GATE can also do machine to machine authentication, what's passed between the machines are a group of symbols [ token ], in that case nothing needs to be displayed on any screen, and therefore there is no button to be seen, just some tokens being exchanged between the machines.
Q 4. When using GATE, do you remember letters or symbols ?
A : Yes, of course, user has to remember the user Id and pins in the passcode. This is the same as traditional password, you need to know what your user Id is and what the pins are in your passcode. What's different between GATE and traditional password is : instead of entering one pin at a time [ which is easily stolen by a hacker/observer ], GATE enters a group of symbols at a time for each user pin, the user pin is mixed in with other symbols, so it becomes obscure. And only the user and the server know whether the tokens entered are valid or not.
Q 5. What would it take to implement this technology, both in terms of equipment and money ?
Contact for details.
Q 6. How can you use GATE to program machines to authenticate each other ?
A : With traditional password, you can use machine A to log into machine B, as long as machine A knows the password, this is the same with GATE, machine A can log into machine B, as long as machine A knows the GATE passcode on machine B. The reason I'm saying this is because some authentication methods only work between human and machine : e.g. finger printing & iris scanning, they can only authenticate human, they can't be used to authenticate a machine. But GATE, like traditional passwords, can be used to authenticate both human and machine.
Q 7. How can GATE be used for information encryption and decryption, what encryption algorithm is used ?
A : It uses the GATE encryption algorithm, it mixes information elements with misinformation elements, then attach valid tokens table and key tokens to the information elements and invalid tokens table and key tokens to the misinformation elements, and sent them out, on the receiver side, authenticate each set of information by checking the attached tokens table and key tokens, then get rid of the misinformation and get the original information. This method is explained in the GATE video : https://www.youtube.com/watch?v=518p2cIbynY
Q 8. Any hashing for the passcode file ?
A : The GATE passcode file is encrypted, not hashed, so the GATE app running on the server can decrypt and read it back to get the user pins, then mix them with other symbols to present them to the user as tokens table. Programmers can select any reliable encryption method they choose, the encryption key can be dynamically generated and it is not saved anywhere so no one can steal it. The encryption key can be generated by mixing some of the following unique and yet stable info : server Id, CPU property, motherboard property, the GATE app Id on the server, hard drive serial number or some other property that is not saved in a file or DB, but the GATE app can get by making a call to the system. That way a hacker won't be able to get the key from a file or DB, and this will make the encryption key safe from being stolen. In case the info gets changed because of a system change [ CPU, motherboard, hard drive failure and need to replace them with a new one and therefore the info used to generate the encryption key needs to change ], then users need to reset their passcodes.
We are forced to update our passwords every 3,4 months with the current password system, with the GATE system, if such changes do happen, just treat it as a forced password update for the sake of safety, shouldn't be too much of an issue, because people are already doing it now with the traditional password system anyway. So the main point is to select some unique [ different from machine to machine, and different from one GATE app to another ] and stable [ so it keeps the same for a long time, therefore users don't have to reset their passcodes too often, assuming you don't change your CPU / motherboard every month ]. The programmer can combine some of the selected properties and get a hashed string, then use that as the encryption key. Therefore this key will be unique when it's running on each machine, even the programmer will not know what the key will be when the GATE runs on a production machine, because when the app runs on development machine, it uses the info from the development environment, but when it's running on a production machine, the info from that environment will be different. Dynamic, unique and stable are the 3 key words here. Sample implementation is in my demo code.
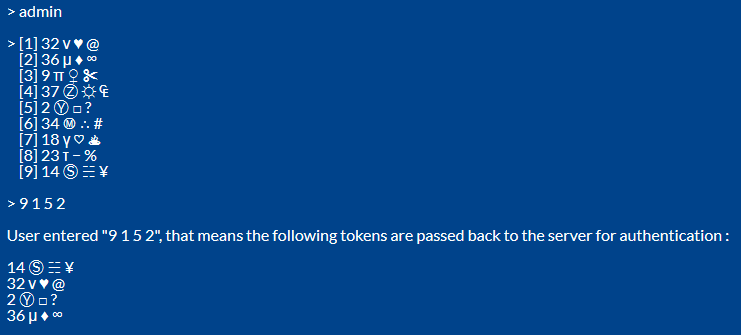
Q 9. What about entering a password into a command prompt when trying to connect through ssh remotely ?
A : It can be done like this : the user first enters Id, the server generates 9 tokens [ like 9 buttons in a UI ], show them to the user on command line, then user enters a number which stands for the index of the token [ each of which may have 4 symbols in that token ], so it looks like this :
Q 10. Do licensing, sample software, and comprehensive training come together as a package ?
A : No, you can pick and choose any of them. For instance if you think you can understand and implement it yourself, you can just license it and do it without the sample software or comprehensive training. Or if you don't want to license it but just want to buy the sample software, you can do just that. Also, if someone just wants to learn the details of this new method, he can do training only without licensing or software.
Q 11. Can I license it for any amount of time ?
A : Yes, on a yearly basis. The longer the better for you, because there is no guarantee that the price is fixed, it might go up as the system gets more and more popular. The longer the license the more protection you have against price increase, at least for the amount of time it is licensed.
Q 12. What locations are available for training ?
A : For now, Atlanta only, as time goes on, there might be more locations or even online training.
Q 13. What languages are available for training ?
A : For now, English and Chinese, as time goes on, there might be more languages.
A : GATE is coming to the market, and available now if you are interested. You can get it in the following formats :
[1] GATE IP License
[2] Software And Training - Sample software : different versions with different levels of functionality and pricing
Q 2. Does the destination computer have knowledge or know how to interpret these symbols ?
A : Only the server that runs GATE has knowledge of the symbols and knows how to interpret them, the client that user logs in is only functioning as input/output device, it knows nothing about how to interpret these symbols, it just passes the info between the server and the user.
Q 3. About the token, is it a physical token that you have to carry around ?
A : No, it's not a physical entity you carry around. I'm just borrowing the word "token" to refer to a group of symbols that are presented to the user, you can easily use other words to mean the same concept : symbols group, or symbol set. The purpose of using a group of symbols is to hide each user pin among other symbols, so the user pin is not obvious to a hacker / observer. When the token [ group of symbols ] is displayed on the screen, they are on a button [ each with 4 symbols ], so in GATE the word token and button are interchangeable. But keep in mind GATE can also do machine to machine authentication, what's passed between the machines are a group of symbols [ token ], in that case nothing needs to be displayed on any screen, and therefore there is no button to be seen, just some tokens being exchanged between the machines.
Q 4. When using GATE, do you remember letters or symbols ?
A : Yes, of course, user has to remember the user Id and pins in the passcode. This is the same as traditional password, you need to know what your user Id is and what the pins are in your passcode. What's different between GATE and traditional password is : instead of entering one pin at a time [ which is easily stolen by a hacker/observer ], GATE enters a group of symbols at a time for each user pin, the user pin is mixed in with other symbols, so it becomes obscure. And only the user and the server know whether the tokens entered are valid or not.
Q 5. What would it take to implement this technology, both in terms of equipment and money ?
| A : |
|
Contact for details.
Q 6. How can you use GATE to program machines to authenticate each other ?
A : With traditional password, you can use machine A to log into machine B, as long as machine A knows the password, this is the same with GATE, machine A can log into machine B, as long as machine A knows the GATE passcode on machine B. The reason I'm saying this is because some authentication methods only work between human and machine : e.g. finger printing & iris scanning, they can only authenticate human, they can't be used to authenticate a machine. But GATE, like traditional passwords, can be used to authenticate both human and machine.
Q 7. How can GATE be used for information encryption and decryption, what encryption algorithm is used ?
A : It uses the GATE encryption algorithm, it mixes information elements with misinformation elements, then attach valid tokens table and key tokens to the information elements and invalid tokens table and key tokens to the misinformation elements, and sent them out, on the receiver side, authenticate each set of information by checking the attached tokens table and key tokens, then get rid of the misinformation and get the original information. This method is explained in the GATE video : https://www.youtube.com/watch?v=518p2cIbynY
Q 8. Any hashing for the passcode file ?
A : The GATE passcode file is encrypted, not hashed, so the GATE app running on the server can decrypt and read it back to get the user pins, then mix them with other symbols to present them to the user as tokens table. Programmers can select any reliable encryption method they choose, the encryption key can be dynamically generated and it is not saved anywhere so no one can steal it. The encryption key can be generated by mixing some of the following unique and yet stable info : server Id, CPU property, motherboard property, the GATE app Id on the server, hard drive serial number or some other property that is not saved in a file or DB, but the GATE app can get by making a call to the system. That way a hacker won't be able to get the key from a file or DB, and this will make the encryption key safe from being stolen. In case the info gets changed because of a system change [ CPU, motherboard, hard drive failure and need to replace them with a new one and therefore the info used to generate the encryption key needs to change ], then users need to reset their passcodes.
We are forced to update our passwords every 3,4 months with the current password system, with the GATE system, if such changes do happen, just treat it as a forced password update for the sake of safety, shouldn't be too much of an issue, because people are already doing it now with the traditional password system anyway. So the main point is to select some unique [ different from machine to machine, and different from one GATE app to another ] and stable [ so it keeps the same for a long time, therefore users don't have to reset their passcodes too often, assuming you don't change your CPU / motherboard every month ]. The programmer can combine some of the selected properties and get a hashed string, then use that as the encryption key. Therefore this key will be unique when it's running on each machine, even the programmer will not know what the key will be when the GATE runs on a production machine, because when the app runs on development machine, it uses the info from the development environment, but when it's running on a production machine, the info from that environment will be different. Dynamic, unique and stable are the 3 key words here. Sample implementation is in my demo code.
Q 9. What about entering a password into a command prompt when trying to connect through ssh remotely ?
A : It can be done like this : the user first enters Id, the server generates 9 tokens [ like 9 buttons in a UI ], show them to the user on command line, then user enters a number which stands for the index of the token [ each of which may have 4 symbols in that token ], so it looks like this :

Q 10. Do licensing, sample software, and comprehensive training come together as a package ?
A : No, you can pick and choose any of them. For instance if you think you can understand and implement it yourself, you can just license it and do it without the sample software or comprehensive training. Or if you don't want to license it but just want to buy the sample software, you can do just that. Also, if someone just wants to learn the details of this new method, he can do training only without licensing or software.
Q 11. Can I license it for any amount of time ?
A : Yes, on a yearly basis. The longer the better for you, because there is no guarantee that the price is fixed, it might go up as the system gets more and more popular. The longer the license the more protection you have against price increase, at least for the amount of time it is licensed.
Q 12. What locations are available for training ?
A : For now, Atlanta only, as time goes on, there might be more locations or even online training.
Q 13. What languages are available for training ?
A : For now, English and Chinese, as time goes on, there might be more languages.